The objective of this post is to outline the following fundamental concepts of cloud computing:
“There is no cloud, it’s just someone else’s computer” is a quip often recited by IT types when explaining the concept of cloud computing to the uninitiated. Whilst the above statement is true to the extent that cloud use typically involves the leasing of remote computing resources from a cloud service provider (CSP), there is, unfortunately, a little more to it than that.
This post targets readers who are new to the cloud, or those who possess a general understanding but may still benefit from a brief refresher (I would also encourage the experts among us to skim through, since our respective interpretations may differ slightly).
My principal intention is to prime the reader for subsequent articles that will provide a more detailed examination of cybersecurity, privacy, risk management, and compliance in the cloud. If you are ready to learn about the essentials of cloud computing, please read on.
A definition of cloud computing
To expand on our initial definition of “somebody else’s computer”, we can consider Cloud computing as:
“the on-demand delivery of IT resources over the Internet with pay-as-you-go pricing.”
The cloud computing model allows customers to access network connectivity, storage, computing power, databases, and software applications on an “as-needed” basis without the requirement to purchase, provide, and maintain hardware and software in physical data centres.
We can further elaborate using the generally agreed-upon U.S. National Institute of Standards and Technology (NIST) definition, which states that cloud computing is:
“a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction.”
Cloud characteristics
Let’s briefly examine the five characteristics of cloud computing, in accordance with the NIST definition:
1. Broad network access
Broad network access simply means that users can consume cloud services over the internet through standard network and application protocols, such as TCP/IP, HTTP and TLS. Cloud services can be accessed via various end-user devices, such as desktops, laptops, tablets, and smartphones.
2. On-demand self-service
On-demand self-service allows the customer, or cloud service consumer (CSC) as we are officially known, to provision computing capabilities such as server time and network storage with a few clicks of a mouse, without the need for human interaction on the part of the provider.
3. Resource pooling
Resource pooling occurs when a cloud service provider combines its computing resources to serve multiple customers simultaneously. Resource pooling is made possible by a distributed computing technology known as virtualisation, which uses a software “hypervisor” to perform hardware abstraction, allowing multiple discrete servers to function as a single, more powerful machine.
Resource pooling creates a multi-tenant environment, where customers share computing resources and rely on logical separation of data by the provider. Whilst customers won’t be able to pinpoint the precise location of the provided resources, they may have the ability to control their geography at a country, state, or data centre level.
4. Rapid elasticity
Cloud elasticity is the ability to rapidly and dynamically allocate cloud resources, including CPU, storage, memory, and bandwidth in response to changing demands.
Cloud elasticity allows for the efficient use of IT resources and prevents over or under-provisioning of a particular service or application. Allocating too many resources can result in unnecessary costs, while allocating too few resources may impact service availability.
5. Measured service
Measured service refers to the “pay-as-you-go” utility billing concept made popular by gas, electricity, and water providers. Employing a metering capability appropriate to the type of cloud service means that resource usage can be monitored, controlled, and reported on, providing transparency for both the provider and consumer.

Cloud deployment models
Cloud deployment models distinguish the administrative entities that control access to a given cloud service. The majority of the time when people mention “the Cloud”, they are referring to the public cloud, although it is certainly worth being aware of the other three deployment models.
Public cloud
The public cloud is the standard commercial model, whereby cloud services are available to the public and administered by a cloud service provider such as Amazon, Microsoft, or Google.
Private cloud
Private clouds are owned and consumed by a single private entity. They may be managed by a third party and be physically located either or off the premises of the owner.
Community cloud
Community cloud infrastructure is shared by several organisations and supports a specific community that has shared concerns e.g. healthcare, scientific research, or the public sector. A community cloud may be managed by its members or by a third party and may be located on or off premises.
Hybrid cloud
A hybrid cloud, as its name suggests, is an amalgamation of two or more of the above deployments (private, community, or public). Each deployment version remains a unique entity, although they are bound together by standardised or proprietary technology that enables data and application portability. The term hybrid cloud is also commonly used to describe a non-cloud data centre bridged directly to a cloud provider.
Cloud service models
The three cloud computing service models are Infrastructure as a Service (Iaas), Platform as a Services (PaaS), and Software as a Service (SaaS). The service model relates to the respective degree of flexibility and control over cloud services attributed to the cloud service provider and cloud service consumer.
Infrastructure as a Service (Iaas)
Infrastructure as a Service, or IaaS, contains the basic building blocks for cloud IT services and typically provides networking features, computing power, memory, and data storage on virtual or dedicated hardware. Infrastructure as a Service presents cloud service consumers with the highest degree of flexibility and management control over IT resources. The consumer is responsible for the installation, configuration, and operation of everything above the computing infrastructure, including the operating system, databases, and application software.
Platform as a Services (PaaS)
Platform as a Service removes the need for consumers to manage the underlying computing infrastructure, such as hardware, operating systems, and databases. In a PaaS environment, the provider takes care of undifferentiated heavy lifting tasks such as procurement, capacity planning, software maintenance, and patching, allowing the consumer to focus on the deployment and management of their applications.
Software as a Service (SaaS)
Despite offering the least amount of flexibility and control on the part of the consumer, its simplicity and utility make Software as a Service the most widely adopted of the cloud service models (I drafted this post on a SaaS application). Software as a Service is essentially an end-user application that is run and managed by the service provider. The consumer is responsible for managing user credentials and other application-specific configuration tasks.
Cloud service providers
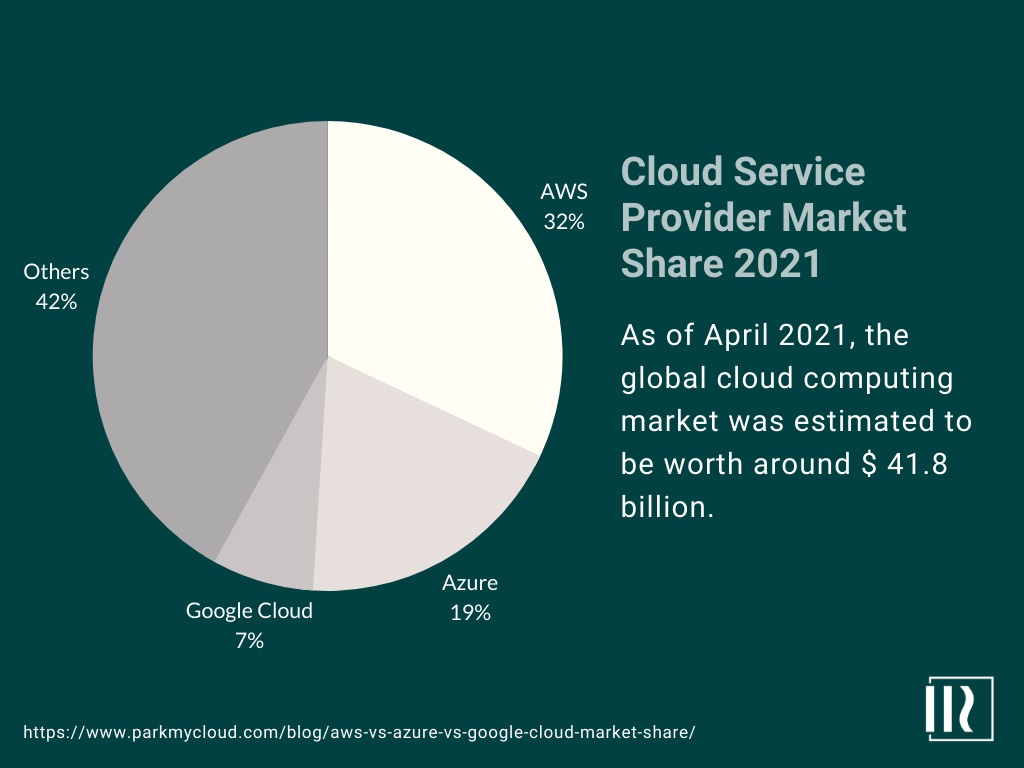
A cloud service provider (CSP) is a third-party organisation that offers cloud-based platforms, infrastructure, applications, or storage services. As of April 2021, the global cloud computing market was estimated to be worth around $41.8 billion. Amazon Web Services (AWS) is the market leader with a 32% market share valued at £13.4 billion, followed by Microsoft Azure (19%) Google Google Cloud Platform (7%), IBM Cloud (IBM Cloud), and a number of smaller players.
The fascinating part about Amazon being the market-leading cloud service provider is that it didn’t start as a technology company. It was an e-commerce company struggling to scale its IT infrastructure to meet growing demand. Those issues forced Amazon to build a global network of state-of-the-art data centres to deal with the rapid growth it was experiencing. The core competencies that the company developed whilst tackling its provisioning problems laid the foundation for what would become Amazon Web Services.
Cloud computing benefits
To say that cloud computing has revolutionised business information technology is by no means an understatement. Let’s take a look at some of the key advantages over traditional on-premise deployments.
Reduction in IT expenditure
Migrating to the cloud allows customers to reduce the cost of owning, managing, and maintaining on-premise infrastructure, hardware, and software systems. Operational expenses can replace capital expenses, and comparative running costs are much lower due to the benefits of economies of scale that the CSP passes on to the consumer.
Increased agility
The cloud allows consumers to develop, test, and launch software applications with great speed and flexibility. On-demand access to a broad range of technologies supports innovation by allowing developers the freedom to experiment by spinning up resources as needed – from infrastructure services, content delivery networks, databases, machine learning, data lakes, analytics, and more.
Resource elasticity
Resource elasticity removes the need to over-provision resources ahead of time to handle peak levels of business activity in the future. The cloud allows consumers to dynamically scale resources up or down to instantly grow and shrink capacity in line with the changing requirements of the application. Resource elasticity reduces energy consumption and improves service availability by increasing resources in line with sudden spikes in utilisation that may have caused a service outage.
Global outreach
Cloud computing allows consumers to launch resources in multiple geographies and create a global deployment in a matter of minutes. The AWS Cloud, for example, spans 25 geographic regions with over 80 independent data centre clusters. The global outreach of the cloud allows consumers to deploy applications close to end-users for reduced latency. Another advantage is that resources can be restricted to specific geographies to align with privacy requirements that limit cross-border transfers of personal data.
Conclusion
The exponential growth of cloud computing as a mechanism for the on-demand delivery of IT resources over the Internet with “pay-as-you-go” pricing, can be directly attributed to the business benefits derived from reduced costs, increased flexibility, resource efficiency, and global coverage. Whilst the cloud has evolved into the de-facto standard computing paradigm for agile business application deployments, cybersecurity and privacy are of critical concern, particularly when entrusting third parties to store and process large quantities of sensitive personal data, such as medical records, on a multi-tenant architecture, accessed via the internet.
This is not to say that the cloud is inherently insecure. On the contrary, if properly managed, it offers numerous security benefits in comparison with traditional on-premise deployments. The key to securing clouds workloads is a comprehensive, risk-based approach that combines the built-in security of the cloud infrastructure, with a framework of governance, policies, procedures, and technical controls to protect the confidentiality, integrity, and availability of sensitive data and the application environment as a whole. More about that in my next post…
Links
Related Posts
How to Assess your Certification Readiness with an ISO 27001 Gap Analysis
This post will provide answers to the following fundamental questions concerning ISO 27001 gap analysis…
Protect Your Digital Life Science Business: The Value of Cybersecurity
Introduction As a digital life science community member, your business is almost certainly on the…
Why medical records are the biggest target for cybercriminals
Introduction The trend in remote working spurred by the COVID-19 pandemic has demonstrated how much…
What is ISO 27001, and why should we certify?
This post addresses the following questions The post targets business leaders considering embarking on an…